With Docker, you have a convenient technology, but it can be a security risk too. It is important to not forget to protect your Docker Engine against possible threats, especially if you're running Docker in production.
In order to understand all the good practices that exist for a Docker installation, you have to concentrate on it. It is possible to get an overview of all the things, but this may trigger some initial inhibitions not dealing with the topic of security and hardening at all.
Fortunately, there is an open-source tool for hardening Docker installations from the Docker developers themselves. It is called "Docker Bench for Security".
This tool is an automated script that can help to find issues with your current configuration. The script scans your host to find weaknesses in your Docker Engine setup.
Running the Script
I think the easiest way to use this Auditing tool is to clone the script from GitHub and run it directly. Since this tool is open source you can have a look at the source code here. In this part, we use Git to clone the repository. After that, we execute the script using our shell. This tool should be run with sudo, as it includes checks that require root access.
git clone https://github.com/docker/docker-bench-security.git
cd docker-bench-security
sudo sh docker-bench-security.shAfter you've executed the command you will see the audit results displayed in your terminal. If you have a large number of containers running then the scan can take a few seconds to a minute.
The Result
The report that falls out is color-coded so that vulnerabilities can be quickly identified:
INFO - divides different scanned sections
PASS - your system met all the requirements
WARN - potential vulnerability
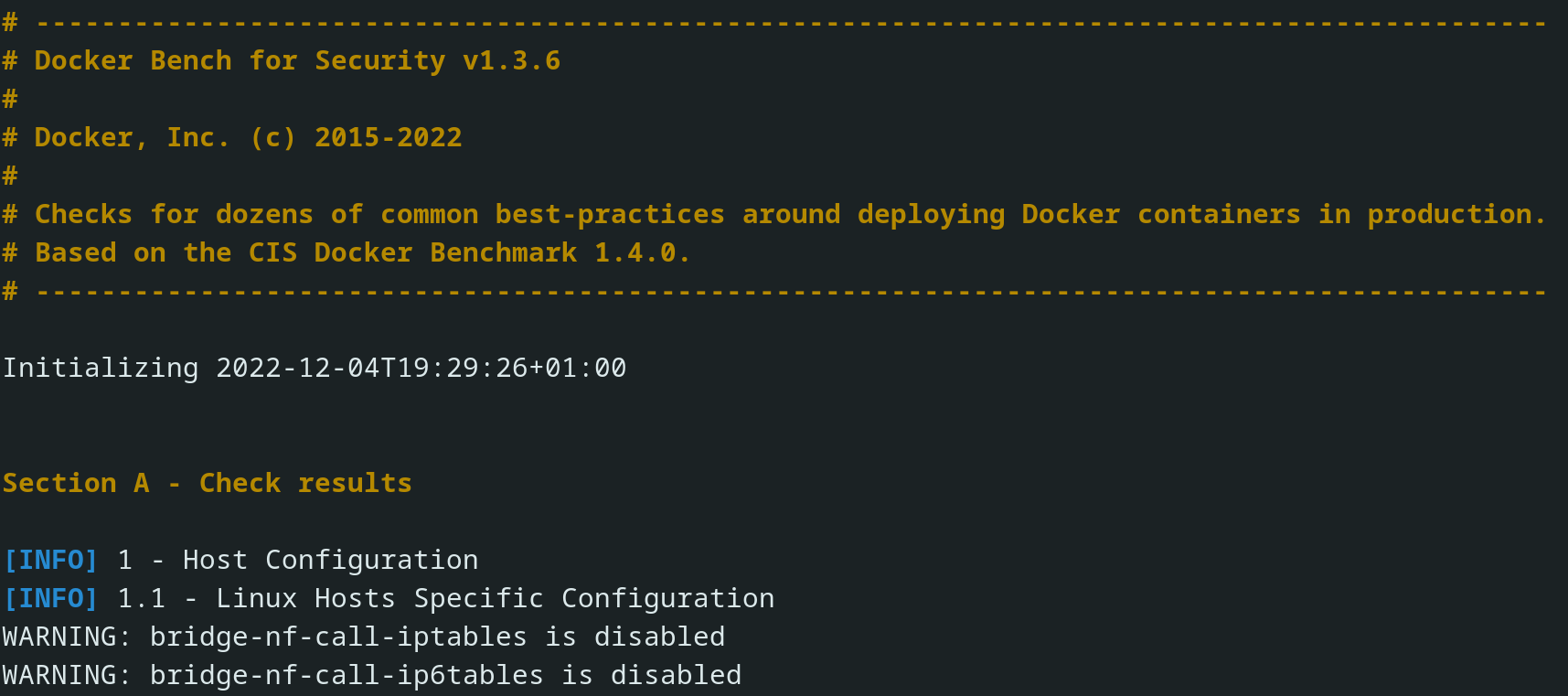
The Docker Bench Security tool runs over 200 individual checks in total. The tests are all automated and based on the CIS Docker Benchmark v1.4.0.
Customize the Report Output
Docker Bench supports several flags that you can use to adjust its output to your personal needs:
-b: Disable colors.
-p: Do not include suggested remediation measures. Helpful when you want to focus on the warnings and reduce the noise in the output.
-l result.txt: Write output to result.txt instead of the terminal.
-e check_5.1,check_5.2: Exclude checks 5.4 and 5.5.
-c check_3.15,check_3.16: Run checks 3.15 and 3.16 only. The test list is available on GitHub.You can combine flags together to produce the report that you need.
Common Issues
If you run this tool against your homelab installation, it is very likely that you will encounter some warnings. Below are a few approaches to how you can eliminate some of these common vulnerabilities.
Note: If you just copy them without knowing what you are doing, your installation may not work as desired anymore!
Strengthening the Daemon
If you never thought about hardening your Docker installation before, Docker Bench will usually find issues with your daemon configuration. Adding the following lines to your /etc/docker/daemon.json will solve several daemon warnings.
It is recommended to add and test one line at a time while building your new daemon.json.
{
"icc": false,
"live-restore": true,
"no-new-privileges": true,
"userland-proxy": false,
"userns-remap": "default"
}- icc: This entry is perhaps the simplest configuration change to make for Docker security. It stops the Docker daemon from automatically adding the Docker image to the default network.
- live-restore: Setting this allows containers to keep running even if the daemon stops. This is advisable in production environments where you want to minimize downtime.
- no-new-privileges: The no-new-privileges entry prevents containers from acquiring any additional rights beyond those granted at startup time.
- userland-proxy: Disabling means that
iptablesis used to route host port traffic into containers. Without it, Docker’s userland proxy process is used, which increases the attack surface of your daemon. - userns-remap: This enables the use of user namespaces, so
rootin a container maps to a less privileged host user. This reduces the risk of a compromised container being able to runrootcommands on your host. Usingdefaultwill instruct Docker to set up a dedicated user account for this purpose.
Enabling Auditing for Docker
Make sure you have auditd installed. Edit your /etc/audit/audit.rules and add the following lines to the bottom of the file:
-w /etc/default/docker -p wa
-w /etc/docker -p wa
-w /etc/docker/daemon.json -p wa
-w /lib/systemd/system/docker.service -p wa
-w /lib/systemd/system/docker.socket -p wa
-w /usr/bin/docker -p wa
-w /usr/bin/docker-containerd -p wa
-w /usr/bin/docker-runc -p wa
-w /var/lib/docker -p waThe -p wa argument means that auditd will log writes and attribute changes that affect the files. If your Docker Bench output suggests that you use auditing for additional directories, add them to the list, too. If you are reading this it may be that new directories have already been added.
After that, you'll need to restart auditd to apply your changes:
sudo systemctl restart auditdSummary
Docker Bench for Security is an extremely useful tool if you want to secure and harden your Docker installation. Since this software is open source, improvements and even community checks are constantly being added, which then flow into the test list. With CIS Docker Benchmark v1.4.0 as the basis for testing, you have a curated list of scenarios. I have used it to harden my private installations and find this tool very useful to first get an overview of potential risks. From this point, you can then dig deeper into hardening and various security topics, keeping in mind that this tool is not the only source of truth.
If you want to use this tool alongside active container vulnerability scanners, you can use Trivy or Clair for example. These tools will help you to identify problems inside your containers.
